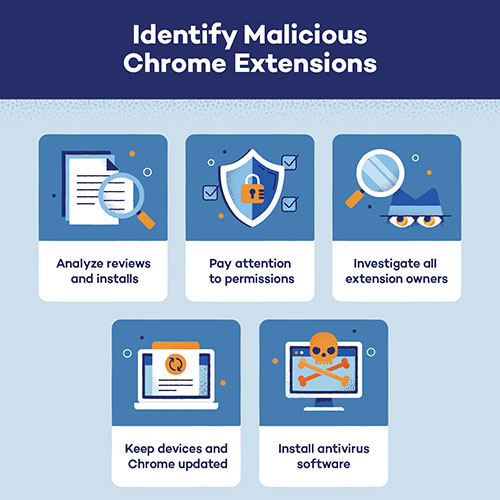
Breaking News

Since January 8, 2025, hackers have been using its IP ranges for global attacks, including scanning systems, stealing passwords, and taking advantage of software bugs.
A new wave of cyber threats has emerged in 2025, as cybersecurity researchers at Trustwave SpiderLabs uncovered a surge in attacks powered by Russian-based Proton66 malware. This recent malware attack 2025 campaign has been traced back to Proton66, a Russian hosting provider now under scrutiny for facilitating widespread cybercriminal activities.
Since January 8, 2025, Russian hackers have been exploiting Proton66’s infrastructure to launch coordinated attacks across the globe. The campaign, now known as the Proton66 hacking campaign, involves aggressive IP-based scanning, credential theft, and exploitation of software vulnerabilities. The most malicious activities stem from IP blocks 45.135.232.0/24 and 45.140.17.0/24, which had no prior history of cyber abuse, suggesting a strategic shift in the attackers’ operational tactics.
Researchers Pawel Knapczyk and Dawid Nesterowicz from SpiderLabs revealed that this campaign is not only stealthy but also far-reaching, impacting organizations across multiple sectors worldwide. The attackers are believed to be linked to a sophisticated Russian cybercrime group that is increasingly using Proton66’s services to mask their identities and distribute malware more effectively.
The Proton66 malware operates by leveraging compromised servers to host malicious payloads and command-and-control systems, making it harder for defenders to isolate the threat. Victims have reported a wide range of consequences, including data breaches, service disruptions, and compromised user credentials.
Cybersecurity experts are urging organizations to monitor traffic from the mentioned IP blocks and update their security systems to detect and mitigate such threats. The recent malware attacks from Russia highlight an alarming trend of state-tolerated or loosely affiliated hacker groups using commercial infrastructure to conduct high-scale operations.
As the Proton66 malware continues to spread, analysts warn that this may be a prelude to more sophisticated attacks targeting critical infrastructure, underlining the importance of proactive defense and international cooperation to combat cyber threats emanating from Russian hackers.
Since January 8, 2025, Russian hackers have been exploiting Proton66’s infrastructure to launch coordinated attacks across the globe. The campaign, now known as the Proton66 hacking campaign, involves aggressive IP-based scanning, credential theft, and exploitation of software vulnerabilities. The most malicious activities stem from IP blocks 45.135.232.0/24 and 45.140.17.0/24, which had no prior history of cyber abuse, suggesting a strategic shift in the attackers’ operational tactics.
Researchers Pawel Knapczyk and Dawid Nesterowicz from SpiderLabs revealed that this campaign is not only stealthy but also far-reaching, impacting organizations across multiple sectors worldwide. The attackers are believed to be linked to a sophisticated Russian cybercrime group that is increasingly using Proton66’s services to mask their identities and distribute malware more effectively.
The Proton66 malware operates by leveraging compromised servers to host malicious payloads and command-and-control systems, making it harder for defenders to isolate the threat. Victims have reported a wide range of consequences, including data breaches, service disruptions, and compromised user credentials.
Cybersecurity experts are urging organizations to monitor traffic from the mentioned IP blocks and update their security systems to detect and mitigate such threats. The recent malware attacks from Russia highlight an alarming trend of state-tolerated or loosely affiliated hacker groups using commercial infrastructure to conduct high-scale operations.
As the Proton66 malware continues to spread, analysts warn that this may be a prelude to more sophisticated attacks targeting critical infrastructure, underlining the importance of proactive defense and international cooperation to combat cyber threats emanating from Russian hackers.
See What’s Next in Tech With the Fast Forward Newsletter
Tweets From @varindiamag
Nothing to see here - yet
When they Tweet, their Tweets will show up here.