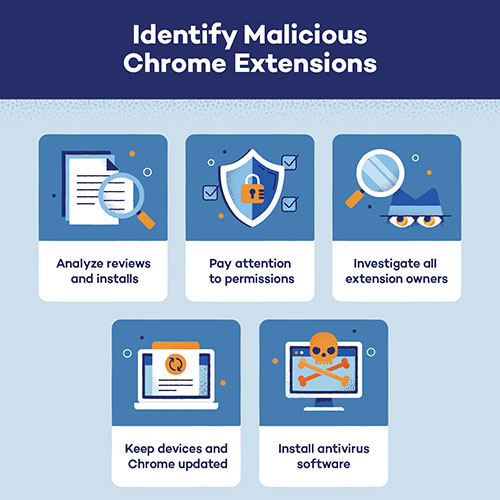
Oracle faces another major cybersecurity setback as a second cyberattack in April 2025 compromises login credentials from a long-dormant system.
In a concerning development, Oracle has confirmed a second cybersecurity breach in a month, deepening worries about the tech giant’s data security infrastructure. The Oracle data breach in April 2025 involved a legacy system that, although inactive for over eight years, still contained valid login credentials — including some issued as recently as 2024. The attacker reportedly exploited this vulnerability to access sensitive information.
This cyberattack on Oracle systems follows closely on the heels of an earlier breach, where stolen Oracle data was discovered being offered for sale on dark web forums. That incident primarily targeted Oracle's cloud server infrastructure in Austin, Texas, raising alarm over potential risks to enterprise customers and sensitive cloud-hosted assets.
According to internal sources, the second cybersecurity attack on Oracle was uncovered when anomalous login activity was detected in the legacy system. While Oracle had long since decommissioned the platform, the presence of still-active credentials left it vulnerable to exploitation. The company acknowledged that the same attacker may be responsible for both breaches and may have demanded an extortion payment in exchange for not releasing the stolen data.
Oracle has alerted the Federal Bureau of Investigation (FBI) and cybersecurity firm CrowdStrike, which are now leading the investigation. Early findings suggest that the hacker may have gained initial access weeks before being detected, prompting a broader review of Oracle’s internal and external-facing systems.
The Oracle breach timeline now includes two incidents within a matter of weeks, both signaling deep-rooted issues related to legacy systems and credential management. Security experts warn that the presence of outdated but still-active systems poses significant risks, especially for enterprises with a vast global footprint like Oracle.
At the time of writing, Oracle has not disclosed the exact number of affected accounts or the scope of data compromised. The company has promised to update customers and stakeholders as the investigation progresses. Both Oracle and CrowdStrike have emphasized the importance of rotating credentials, deactivating unused systems, and implementing zero-trust security frameworks to prevent further incidents.
This string of breaches marks a pivotal moment for Oracle as it attempts to restore confidence among enterprise clients and regulators. With cybersecurity threats escalating globally, organizations are being urged to conduct rigorous audits of legacy infrastructure and enforce stricter access controls.
Also Read: Oracle Strengthens Partner Strategy at CloudWorld Tour Mumbai
See What’s Next in Tech With the Fast Forward Newsletter
Tweets From @varindiamag
Nothing to see here - yet
When they Tweet, their Tweets will show up here.