Breaking News
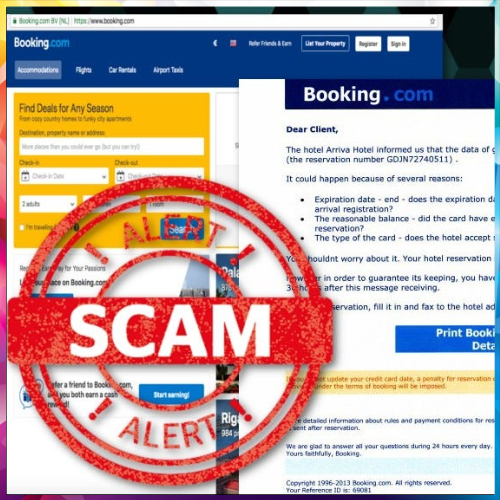
The incident of Robert underscores a rising cybersecurity threat where attackers infiltrate trusted hospitality platforms, turning them into tools for phishing.
A growing wave of phishing scams is targeting travelers using legitimate online booking platforms, and the latest incident involving Booking.com has raised serious concerns. A sophisticated travel scam recently duped Robert Woodford, a recruitment marketing expert, into paying fake hotel fees after booking a hotel in Verona via Booking.com.
What makes this incident particularly alarming is the method used. After completing a legitimate hotel reservation, Woodford received a follow-up message within Booking.com’s official chat thread—not through email or text—asking for “missing details” and a prepayment. To verify its authenticity, Woodford logged in directly to Booking.com rather than clicking any external links. Shockingly, the same message was visible within the platform, complete with a realistic-looking payment link featuring “bookingcom” in the URL.
Believing it to be genuine, he made the payment, only to later realize that the transaction went to a fraudulent account. This fake hotel prepayment scam demonstrates how cybercriminals are now infiltrating legitimate platforms, manipulating their internal systems or exploiting trusted interfaces to deceive users.
The implications go beyond travelers. Cybercrime in the hospitality industry is now targeting both hotel staff and guests, using fake CAPTCHAs, malware, and phishing links to access booking data and hijack communication channels.
Experts urge travelers to take extra precautions: avoid making payments through links in messages, even those appearing within trusted apps; confirm requests directly with the hotel via phone; and use credit cards with fraud protection. Platforms like Booking.com are also being called upon to enhance their cybersecurity infrastructure and better safeguard user communications.
This Booking.com scam is a wake-up call for travelers and businesses alike—even verified systems can be compromised, and vigilance is now more critical than ever.
What makes this incident particularly alarming is the method used. After completing a legitimate hotel reservation, Woodford received a follow-up message within Booking.com’s official chat thread—not through email or text—asking for “missing details” and a prepayment. To verify its authenticity, Woodford logged in directly to Booking.com rather than clicking any external links. Shockingly, the same message was visible within the platform, complete with a realistic-looking payment link featuring “bookingcom” in the URL.
Believing it to be genuine, he made the payment, only to later realize that the transaction went to a fraudulent account. This fake hotel prepayment scam demonstrates how cybercriminals are now infiltrating legitimate platforms, manipulating their internal systems or exploiting trusted interfaces to deceive users.
The implications go beyond travelers. Cybercrime in the hospitality industry is now targeting both hotel staff and guests, using fake CAPTCHAs, malware, and phishing links to access booking data and hijack communication channels.
Experts urge travelers to take extra precautions: avoid making payments through links in messages, even those appearing within trusted apps; confirm requests directly with the hotel via phone; and use credit cards with fraud protection. Platforms like Booking.com are also being called upon to enhance their cybersecurity infrastructure and better safeguard user communications.
This Booking.com scam is a wake-up call for travelers and businesses alike—even verified systems can be compromised, and vigilance is now more critical than ever.
See What’s Next in Tech With the Fast Forward Newsletter
Tweets From @varindiamag
Nothing to see here - yet
When they Tweet, their Tweets will show up here.