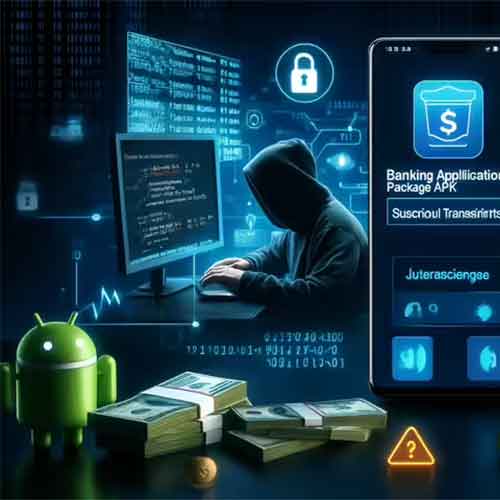
Cybersecurity agencies are warning of a growing fraud technique involving OTP forwarding through malicious APK files hosted outside the country, posing serious risks to mobile banking and digital payment users. In this attack, victims are tricked into downloading an Android application from unofficial links shared via SMS, WhatsApp, email, or fake customer-support calls.
Once installed, the APK requests excessive permissions, including access to SMS, notifications, and accessibility services. This allows the malware to silently intercept one-time passwords (OTPs) sent by banks, wallets, and government platforms, and forward them in real time to servers hosted overseas. Fraudsters then use these OTPs to authorize transactions, reset credentials, or take over accounts without the user’s knowledge.
Unlike traditional phishing, APK-based attacks bypass browser security and app-store vetting, making detection harder. Hosting command-and-control servers outside India further complicates investigation, jurisdiction, and takedown efforts.
Experts warn that such attacks are increasing alongside the rise of instant digital payments and app-based authentication. Users are advised to download apps only from official app stores, deny unnecessary permissions, and treat unsolicited APK links as high-risk. For enterprises and banks, stronger behavioral monitoring and device-level fraud detection are becoming essential to counter this evolving threat.
See What’s Next in Tech With the Fast Forward Newsletter
Tweets From @varindiamag
Nothing to see here - yet
When they Tweet, their Tweets will show up here.