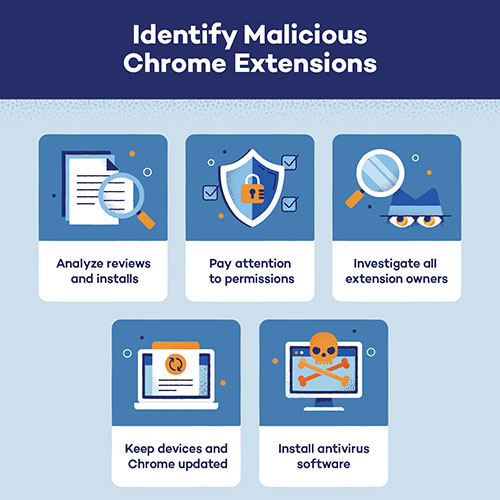
The Indian Computer Emergency Response Team’s (CERT-In’s) norms have raised quite the ruckus among enterprises and users alike. While the norms were first announced back in April this month, the deadline for complying with them was pushed to September 25 in June.
While it is heartening for the security community to see the Indian government finally take interest in cybersecurity legislations, there are some big problems with the CERT-In’s norms too.
For instance, the rules require companies to report security incidents within six hours of becoming aware of them. They also have a broad definition of security incidents, which could make enterprises liable for not reporting something as simple as a poorly conducted phishing attack at times. Of course, there’s also the rule that requires virtual private network (VPN) service providers to store information on their users, monitor their usage, and maintain servers within India.
These rules have been opposed widely, by the largest tech companies out there, like Facebook etc. They have also been opposed by industry bodies, not just from India, but also overseas. For example, in May, in a letter signed by no less than 11 industry bodies from the European Union, the United Kingdom and the United States, raised concerns over the six-hour timeline, an “overbroad” definition of reportable incidents and more.
The signatories include large and powerful industry bodies like the Bank Policy Institute, the US Chamber of Commerce, and US-India Strategic Partnership Forum, the US-India Business Council, and more. The letter also said that the CERT-In’s rules were “onerous” in nature.
However, while the future of the CERT-In’s rules may not be clear till at least September 25, and probably for months after that, enterprises can and should take steps. Even if the rules are changed to some extent, it’s unlikely that all of the compliance norms will be dropped. In fact, with India’s National Cybersecurity Policy being in the works for over a year now, it’s good form to adopt security compliant products, for all companies, irrespective of their size.
Security firms like Vehere and Crowdstrike offer a host of policy compliant security products, which can not only provide early notifications for cyber incidents, but also keep a log of such incidents.
Enterprises today need to adopt security platforms that provide a wide coverage of malware, including the likes of ransomware, backdoors, distributed denial of service (DDOS), SQL Injection, cross-site scripting attacks, and more. They should also look for tools that provide indicators of compromise (IOC) and indicators of attack (IOA), which allow early detection of compromises too.
There’s, of course, a lot more to getting the right kind of cybersecurity that should be in place. For instance, tools that support Trusted Automated Exchange of Indicator Information (TAXII), allow seamless sharing of cyber threat information across an enterprise’s products, services and even organizational boundaries.
But irrespective of what tools enterprises adopt, one of the key ingredients for being truly compliant of any country’s CERT’s guidelines is employee education. Enterprises should continuously train their employees on the right security practices, how to recognize phishing emails and messages, etc. Even the best cybersecurity tools can’t protect against a hack if users (in this case the employees) aren’t responsible enough.
See What’s Next in Tech With the Fast Forward Newsletter
Tweets From @varindiamag
Nothing to see here - yet
When they Tweet, their Tweets will show up here.