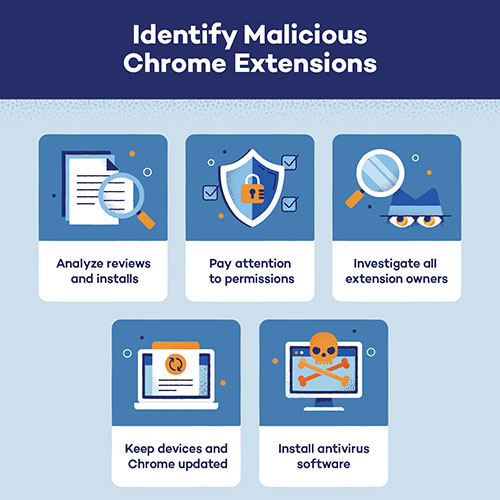
As cyber threats become more sophisticated and relentless, the responsibility of safeguarding digital ecosystems extends far beyond end users and service providers. A crucial yet often overlooked stakeholder in this battle is the Original Equipment Manufacturer (OEM). By embedding security into the very core of hardware and infrastructure, OEMs serve as the first line of defense in protecting enterprises, governments, and consumers against the evolving cybercrime landscape.
This feature explores how leading OEMs and cybersecurity trailblazers are reshaping the narrative of digital security through innovation, collaboration, and a strong focus on secure-by-design principles. Their role goes beyond supplying hardware; they are actively setting new benchmarks, adopting advanced technologies, and building resilient frameworks that can withstand today’s threats while preparing for tomorrow’s challenges.
To understand the strategies shaping this transformation, VARINDIA spoke with leading cybersecurity leaders who shared their perspectives on critical aspects: the integration of new-age technologies for proactive threat detection, the evolution of solutions to stay ahead of attackers, mechanisms to secure firmware, BIOS, and embedded systems, and the anticipated impact of quantum computing on the OEM security roadmap. Together, these insights underscore the indispensable role of OEMs in building a safer and more resilient digital future.
-------------------------------------------------------------------------------------------------------------------------------------------
Fortinet pioneers cybersecurity with AI, Zero Trust, and quantum-safe tech
 VIVEK SRIVASTAVA
VIVEK SRIVASTAVA
COUNTRY MANAGER, INDIA & SAARC, FORTINET
Fortinet’s integrated platform approach, built on FortiOS—the common operating system across FortiGate, SD-WAN, and SASE—is the key to proactively detecting and preventing threats. Most customers begin with our ASIC-powered FortiGate firewall, expand into SD-WAN, and then adopt FortiSASE. Since all core SASE functions are natively built into a single OS, we deliver better performance and security, reduce total cost of ownership, and simplify operations—making us unique in the industry. Fortinet is also uniquely positioned in the growing OT security market, recognized as a leader in the Westlands Advisory Report, which reflects over a decade of focused investment and product development.
We’ve been investing in AI for over 15 years and hold more than 500 issued and pending AI patents—more than any other cybersecurity company. Our AI tools—FortiAI-Assist, FortiAI-Protect, and FortiAI-SecureAI—are embedded across over a dozen products, enabling automated threat detection, AI infrastructure protection, and accelerated response. We also champion secure-by-design practices, embedding security from the ground up. As a first signatory of CISA’s Secure by Design Pledge, we support raising cybersecurity standards by embedding secure practices into every stage of product development. As quantum computing emerges, Fortinet remains committed to helping customers stay protected. With FortiOS 7.6, solutions like FortiGate NGFW and Fortinet Secure SD-WAN now include built-in quantum-safe features, protecting against harvest-now, decrypt-later attacks and enabling a smooth, secure transition to post-quantum security.
--------------------------------------------------------------------------------------------------------------------------------------------
Trellix advances AI-driven cybersecurity with Trellix Wise platform
 GANESH IYER
GANESH IYER
MANAGING DIRECTOR, INDIA AND SAARC, TRELLIX
Trellix has integrated AI and machine learning into its security platform to detect and neutralize threats in real time. At the core is Trellix Wise, our generative AI-powered foundation that analyzes telemetry from a vast ecosystem of endpoints and network sources. By correlating signals across multiple hybrid environments, it surfaces genuine threats faster, reduces false positives, and enables automated, intelligence-driven responses—improving analyst efficiency fivefold and reducing Mean Time to Response (MTTR) by up to 50%.
We continuously enhance our platform to address evolving threats. Recent advancements include hyper automation for alert investigation, natural-language search for incident data, and integration with a broader range of third-party tools—three times more than many competitors—ensuring greater visibility across hybrid environments. Trellix processes over 68 billion security queries daily and uses this scale to adapt defenses quickly. Enriched threat intelligence from the Trellix Advanced Research Center delivers both speed and precision in countering sophisticated attacks.
Trellix Wise automates triage, investigation, and contextual reporting, saving 8 hours of analyst time per 100 alerts. It supports multilingual interaction, natural language playbook creation, and automated incident summaries, allowing SOC teams to focus on high-value tasks. Trellix also maintains a vast threat intelligence ecosystem, enriched with telemetry, contextual insights, and feeds from Intel 471 and CISA. Through partnerships like the Cyber Threat Alliance and JCDC, and our open-source Data Exchange Layer, we strengthen threat sharing and collective cybersecurity defense.
--------------------------------------------------------------------------------------------------------------------------------------------
Securonix leads autonomous cyber defense with GenAI and quantum readiness
 DIPESH KAURA
DIPESH KAURA
COUNTRY DIRECTOR - INDIA & SAARC, SECURONIX
Securonix, a five-time Gartner Magic Quadrant Leader in Cybersecurity for SIEM, continues to push boundaries in transforming reactive SOC operations into proactive and autonomous digital defense. The Securonix EON platform, embedded with GenAI agents, enables faster threat detection, investigation, and smart response. It is a future-proof platform that unifies SIEM, SOAR, UEBA, and Data Pipeline Management, scaled with Agentic AI, and brings autonomous decision-making to security operations.
Securonix Unified Defense SIEM integrates advanced threat detection, real-time analytics, and automated response mechanisms to help organizations proactively protect their assets. Additionally, Securonix Investigate incorporates ChatGPT-powered GenAI to assist analysts, threat hunters, and administrators in rapidly investigating and responding to threats.
Securonix ensures its platform is constantly evolving to stay ahead of threat actors. We’ve been harnessing AI for over a decade, with our UEBA technology—driven by machine learning and mathematical models—trained on large datasets since 2007. Our innovation is backed by six patents, some dating back to 2015. Unified Defense SIEM merges UEBA capabilities for broader coverage of cyber and insider threats. In August 2023, we launched Securonix Investigate, followed by the April 2025 release of GenAI agents in EON.
Quantum computing, though still emerging, will transform SOC operations by processing vast volumes of data with unprecedented speed. OEMs must adopt post-quantum cryptographic standards and prepare security infrastructure to address new risks and safeguard digital trust.
--------------------------------------------------------------------------------------------------------------------------------------------
Quick Heal pioneers AI-first cybersecurity and quantum-ready defense
 DR. SANJAY KATKAR
DR. SANJAY KATKAR
JOINT MANAGING DIRECTOR, QUICK HEAL TECHNOLOGIES LIMITED
At Quick Heal Technologies, we have embraced an AI-first approach to cybersecurity. Our GoDeep.AI technology integrates traditional machine learning with deep learning, large language models, and NLP—a journey that began over two decades ago with malicious URL detection. Today, this powers both our Quick Heal retail solutions and Seqrite enterprise offerings. We recently adopted a freemium model for AntiFraud.AI, India’s first fraud prevention solution, to increase accessibility. On the enterprise side, the Seqrite Intelligent Assistant (SIA) enables instant threat analysis and response recommendations. Additionally, our cloud-native metaProtect platform supports remote security management, while behavioural analytics help identify zero-day threats, moving us from reactive to predictive defense.
The cyber threat landscape has evolved from high-volume attacks to sophisticated, AI-driven campaigns. We counter this with three key strategies: behavioural pattern recognition instead of signature-based detection, real-time cloud intelligence via Seqrite Labs, and security convergence— unifying endpoint, network, and cloud protection for comprehensive visibility. We are focused on mitigating threats like AI-generated phishing, deepfake social engineering, and supply chain attacks that bypass traditional defenses.
Quantum computing represents the next major cryptographic disruption since the internet’s creation. By the 2030s, RSA and ECC encryption will become obsolete, requiring organizations to migrate to post-quantum cryptography before practical quantum cryptanalysis emerges. This challenge is as much economic and operational as technical. Treating quantum computing as both a threat and opportunity, early adopters will gain long-term security and competitive advantage.
---------------------------------------------------------------------------------------------------------------------------------------------
Kyndryl reinvents cybersecurity with AI- driven, zero trust approach
 HARISH SONI
HARISH SONI
SECURITY AND RESILIENCY LEADER, KYNDRYL INDIA
AI has rewritten the rules of cybersecurity, removing traditional perimeters and rendering legacy systems inadequate. Threat actors are weaponizing it to launch large-scale phishing campaigns, produce convincing deepfakes, clone voices, and uncover system vulnerabilities at unprecedented speed. For India’s BFSI, healthcare, manufacturing, and telecom sectors, the challenge is amplified as they safeguard vast volumes of sensitive data against an increasingly intelligent and adaptive adversary.
Kyndryl’s strategy prioritizes proactive prevention over reactive defense. AI and machine learning are embedded into the security architecture to predict threats, identify anomalies in real time, and act before damage occurs. This is reinforced through a Zero Trust framework that treats every access request as unverified and enforces continuous, rigorous validation. Attack Surface Management (ASM) is central to this approach, enabling continuous identification, assessment, and reduction of potential entry points across networks, applications, cloud environments, endpoints, and human factors. When paired with advanced threat intelligence, this delivers high-fidelity, contextualized data that is rapidly integrated into security workflows to counter evolving attack vectors.
Thus, to stay ahead in this environment, Kyndryl is building a security ecosystem designed to evolve as fast as the threat landscape changes. This means embedding intelligence into every layer of defense, enabling rapid decision-making, and ensuring security strategies grow stronger with each attempted attack. The goal is to create an adaptive foundation capable of protecting critical assets, supporting regulatory compliance, and enabling innovation in the face of constant disruption.
------------------------------------------------------------------------------------------------------------------------------------------
Cohesity transforms backup into AI-powered, zero trust defense
 MAYANK MISHRA
MAYANK MISHRA
REGIONAL DIRECTOR - SALES, INDIA AND SAARC, COHESITY
Cybercriminals are increasingly targeting backup data alongside production systems, making traditional backup strategies inadequate. At Cohesity, we’ve shifted the role of backups from passive insurance to active defense by embedding AI, machine learning, and zero-trust principles into our data security workflows. Our threat intelligence and anomaly detection capabilities continuously scan environments for signs of ransomware and suspicious activity—like rapid encryption or unusual file access—enabling early detection and faster response.
Immutability is a central focus: backups are stored on WORM (write-once, read-many) file systems so data cannot be altered or deleted, even if insider credentials are compromised. Multi- factor authentication and quorum approvals add another layer of protection. With Cohesity Gaia, our generative AI platform, teams can use natural language to assess risk, run compliance checks, and gain actionable insights—turning backup data into a proactive intelligence layer.
As attackers evolve, so must recovery. Our platform is built with immutability and zero trust at its core. Access is tightly controlled, anomalies are flagged in real time, and large-scale recovery can be executed within hours—minimizing business disruption. Following our merger with Veritas, we now protect more workloads across hybrid and multi-cloud environments. And with the rise of quantum computing, we’re proactively implementing quantum-proof encryption in NetBackup 11.0 across all major communication paths, helping organizations safeguard sensitive encrypted data against both current and future threats.
------------------------------------------------------------------------------------------------------------------------------------------------
AI, automation, and quantum readiness reshape enterprise threat defense
 NAN HAO MAGUIRE
NAN HAO MAGUIRE
FIELD CTO - APJC, CLOUDFLARE
New-age technologies for threat management go beyond traditional controls. We leverage AI, automation, cloud-native design, and real-time data to proactively predict, detect, and mitigate threats before harm is materialised. Integration is key—though complex—and a multi-layered, proactive approach helps ensure that the Security Operations Center (SOC) can function intelligently, adaptively, and in real-time. AI supports threat detection, anomaly and behaviour analysis, and alert prioritisation; automation enables faster triage, incident response, and predefined playbook execution; and moving SOC tools to the cloud improves efficiency, scalability, and reduces operational overhead. To stay ahead of the growing cybercrime landscape, constant technology evolution is essential.
Organisations must adopt intelligent, predictive, integrated, and adaptive approaches. A few important steps include: implementing AI-enabled tools for real-time data collection, continuous self- learning, and proactive defense; migrating infrastructure and applications to the cloud for scalability and a unified monitoring environment; consolidating vendors and tools to minimise third-party risks; automating incident response processes; and adopting zero-trust models for continuous authentication, behavioural analysis, and restricting attack movement.
The rise of quantum computing is already influencing OEM security roadmaps. Quantum threats could break traditional encryption like RSA, ECC, and even symmetric algorithms, posing risks to long-lifecycle OEM devices. Although not an immediate threat, the risk is real, and preparation must begin now by embedding post-quantum cryptographic algorithms into OEM firmware, software, and hardware platforms to counter potential ‘harvest now, decrypt later’ attacks.
----------------------------------------------------------------------------------------------------------------------------------------------
AI, platformization and crypto-agility define future of cybersecurity
 HUZEFA MOTIWALA
HUZEFA MOTIWALA
SENIOR DIRECTOR, TECHNICAL SOLUTIONS, INDIA AND SAARC,
PALO ALTO NETWORKS
The pace of cyber-attacks today demands a prevention-first mindset, not a repair-later approach. That’s why we’ve embedded AI, machine learning, and automation across our platforms—spanning network security, cloud, and operations—to identify and block threats in real time. Attackers are increasingly leveraging AI, so organizations must counter with continuous, adaptive AI-powered defenses that can detect, prevent, and respond instantly. Our Precision AI strategy, fuelled by rich threat data and automation, helps us protect over 770,000 customers worldwide, including nine of the Fortune 10, by surfacing threats faster and ensuring defenses evolve at the speed of attackers.
Tackling cybercrime with bolt-on, point solutions may appear effective in the short term, but at scale it creates blind spots and inefficiencies. Fragmented security—averaging 83 tools across 29 vendors—is not just inconvenient, it’s dangerous. That’s why our roadmap focuses on platformization, unifying prevention, detection, and response into one architecture. This approach enables enterprises to detect threats 72 days faster and contain them 84 days sooner, with ROI gains of 101%, compared to just 28% for non-platformized peers.
Looking ahead, quantum computing will eventually make today’s public-key cryptography obsolete, so OEMs must prepare now. Our strategy emphasizes true crypto-agility—deploying quantum-safe algorithms aligned with emerging NIST standards, ensuring open interoperability, and enabling seamless, rapid upgrades as threats and standards evolve. Security, therefore, is no longer just a cost center but a powerful strategic enabler for the digital future
----------------------------------------------------------------------------------------------------------------------------------------------
Kaspersky emphasizes proactive security to ensure long-term cyber resilience
 JAYDEEP SINGH
JAYDEEP SINGH
GENERAL MANAGER - INDIA, KASPERSKY
Kaspersky stays ahead of evolving cyberthreats by integrating advanced technologies like machine learning, behavioral analytics, and real-time threat intelligence into its solutions. As highlighted in the Q1 2025 Threat Landscape for Industrial Automation Systems, we are seeing a rise in complex and targeted attack vectors. To counter this, we use proactive detection methods that combine deep system visibility with AI-powered anomaly detection, enabling our systems to not only recognize known threats but also identify suspicious behaviour patterns that could indicate previously unseen risks. In industrial environments, this allows us to isolate and neutralize malicious activity before it spreads, without disrupting operations.
Our solutions continue to evolve as attackers employ more stealthy and persistent techniques, particularly against industrial automation systems. We are enhancing our Industrial CyberSecurity technologies with behaviour-based detection, anomaly monitoring, and expanded threat intelligence feeds. By investing in machine learning models and automated threat analysis, we can anticipate threats, detect subtle compromise indicators early, and defend against both common malware and advanced persistent threats (APTs).
We also protect firmware, BIOS, and embedded systems through our KasperskyOS-based Cyber Immune approach, which ensures systems are secure by design. Secure boot, strict access controls, real-time integrity checks, and segmentation prevent tampering or lateral movement, even against zero-day threats. Moving forward, the rise of quantum computing could render today’s encryption obsolete. We are already exploring quantum-safe strategies and post-quantum cryptography, encouraging OEMs to embed future-proof encryption into devices now to stay resilient.
----------------------------------------------------------------------------------------------------------------------------------------------
Check Point advances proactive cyber defense with AI and post-quantum security
 MANISH ALSHI
MANISH ALSHI
SR. DIRECTOR - CHANNELS & ALLIANCES, CHECK POINT SOFTWARE TECHNOLOGIES, INDIA & SOUTH ASIA
At Check Point Software, we integrate AI, machine learning, and cloud-delivered intelligence across our Check Point Infinity Platform to ensure threats are detected and prevented in real time. Our ThreatCloud AI leverages over 55 AI engines and makes more than 4 billion security decisions daily, enabling proactive defense against known and unknown threats. We embed AI across all our solutions such as Check Point Harmony Email & Collaboration for securing communications and Check Point Quantum IoT Protect for IoT devices, ensuring organizations can secure endpoints, collaboration tools, and connected environments without disruption. By unifying prevention-first security across network, cloud, email, and IoT, enterprises can stay a step ahead of sophisticated cyberattacks. Cybercrime is becoming increasingly automated, adaptive, and AI-driven, and our solutions evolve accordingly. We are enhancing prevention-first capabilities with AI-powered SOC co-pilots, deepfake detection, and predictive threat intelligence. Our AI-enhanced defenses detect phishing and DNS attacks with five times greater accuracy than traditional tools, while Quantum IoT Protect secures devices at both the firmware and network levels. The Check Point Infinity Platform further consolidates security across hybrid and multi-cloud environments, reducing complexity and maximizing resilience.
Quantum computing represents both an opportunity and a challenge. While it will unlock innovation in AI and other fields, it also poses a threat to current encryption. That is why we are investing in quantum-resistant cryptography, exploring post-quantum algorithms, and working with OEM partners to integrate quantum-safe protocols, ensuring joint solutions protect customers in the quantum era.
------------------------------------------------------------------------------------------------------------------------------------------
Sequretek leverages AI and CTEM to redefine cybersecurity
 PANKIT DESAI
PANKIT DESAI
CO-FOUNDER, SEQURETEK
A fundamental limitation of traditional cybersecurity technologies has been their rule-based architecture, which depended heavily on human intervention. This made threat detection labour- intensive and prone to oversight. At Sequretek, we’ve adopted AI and ML to shift away from this reactive model. These technologies now enable autonomous identification of evolving threats, reduce human dependency, and transform threat detection and response. AI helps recognise malicious patterns in real-time and adapt to novel attack techniques, while also addressing alert fatigue by filtering telemetry and escalating only high-risk anomalies.
As cybercrime becomes more sophisticated—with AI-driven phishing, polymorphic malware, and evasive attacks—we continue to evolve. We follow a ‘human-in-the-loop’ model that combines AI efficiency with human judgment to refine decision-making and defense strategies. Our flagship solution, Percept CTEM, delivers Continuous Threat Exposure Management by closing visibility gaps, scoring risk based on CVSS+EPSS, and identifying and prioritizing vulnerabilities using AI and business-contextual intelligence. It integrates with third-party tools and the broader Percept Security Suite to ensure complete threat coverage. Looking ahead, quantum computing presents a significant cryptographic threat with the potential to break widely used encryption algorithms like RSA, ECC, and even symmetric ones. We're actively integrating quantum-resilient capabilities into our roadmap, ensuring customers remain secure against future risks. By aligning AI, continuous threat exposure management, and forward-compatible quantum-safe strategies, Sequretek is redefining what modern, proactive cybersecurity must look like to stay ahead of both current and emerging threats.
-----------------------------------------------------------------------------------------------------------------------------------------------
Barracuda empowers cyber resilience with AI- driven, integrated security platform
 PARAG KHURANA
PARAG KHURANA
COUNTRY MANAGER - INDIA, BARRACUDA
Barracuda has been leveraging artificial intelligence for the last 10 years, and AI underpins everything we do. For Barracuda, AI is a force multiplier that enables faster threat and incident detection, deeper insights, and more proactive defence. Our AI-powered security platform and managed XDR service are built to meet the needs of Indian organisations facing a rapidly evolving threat landscape. As generative AI drives increasingly sophisticated attacks, Barracuda’s multimodal AI analyses threats across formats like images and QR codes using layered intelligence and real-time behavioural analysis. This helps organisations identify and neutralise threats that traditional tools often miss.
Cyber-attacks are becoming more complex, sophisticated, and difficult to manage—placing pressure on IT teams that need to respond quickly and effectively. Many Indian organisations are managing too many disconnected security tools, leading to gaps, increased costs, and slower response times. Our AI-powered security platform, BarracudaONE, addresses this by consolidating multiple security capabilities into a single, integrated solution. This includes managed XDR, automated incident response, and advanced threat detection. It reduces security complexity, improves visibility, and delivers a more agile, scalable defence. This ensures that even small IT teams can stay resilient in the face of evolving cyber threats.
With AI at the core, Barracuda continues to empower organisations to stay ahead of modern cyber risks through innovation, integration, and real-time threat response.
-----------------------------------------------------------------------------------------------------------------------------------------------
F5 ADSP delivers unified AI protection and quantum-ready security
 PRATIK SHAH
PRATIK SHAH
MANAGING DIRECTOR - INDIA & SAARC, F5
To deliver effective digital experiences today, organizations must carefully balance performance and security across hybrid and multicloud environments. Our recent AI strategies report revealed that while 71% of companies are adopting AI to enhance security, only 2% feel prepared to scale. This gap underscores the pressing need for proactive, integrated protection where applications and APIs operate.
The F5 Application Delivery and Security Platform (ADSP) is designed to address these challenges by unifying application delivery, security, and optimization. With AI-driven solutions such as Distributed Cloud WAAP and Advanced WAF, ADSP enables enterprises to detect anomalies, block bots in real time, and protect workloads seamlessly, whether they are on-premises, in the cloud, or across distributed environments.
Looking ahead, the growing impact of quantum computing makes post-quantum cryptography (PQC) readiness essential. Cyber adversaries are already executing “harvest now, decrypt later” attacks, collecting encrypted data today with the intent to break it once quantum capabilities mature. Supported by decades of cryptographic leadership, F5 ADSP delivers end-to-end PQC through NIST- approved algorithms, securing both client and server environments across hybrid, multicloud, and even legacy systems—without requiring costly infrastructure overhauls.
By combining cutting-edge technical innovation with strong ecosystem collaboration, F5 helps enterprises and OEM partners build secure-by-design ecosystems. This approach ensures organizations remain resilient against today’s AI-driven threats while staying prepared for the challenges of the quantum future.
----------------------------------------------------------------------------------------------------------------------------------------
Tenable advances AI exposure management with unified cybersecurity platform
 RAJNISH GUPTA
RAJNISH GUPTA
MANAGING DIRECTOR AND COUNTRY MANAGER, TENABLE INDIA
As businesses race to adopt GenAI to boost productivity, they are inadvertently creating a new, complex, and often invisible frontier of exposure. Security teams lack visibility into how employees use these powerful tools, what sensitive data might be exposed, and how attackers could manipulate them. To help organisations address these risks, Tenable announced a significant expansion of its market-leading Tenable One platform with the launch of Tenable AI Exposure—a comprehensive solution to see, manage, and control the risks introduced by GenAI. This is a critical step in the evolution of exposure management.
We recognise that CISOs are tired of managing dozens of disparate tools, so our evolution began by creating Tenable One—a unified platform that consolidates their view of risk into a single source of truth. But beyond consolidation, we understand that security teams are overwhelmed with alerts and need clarity, not noise. That’s why Tenable One continues to evolve with embedded AI and analytics to deliver prioritised, actionable guidance—shifting the focus from identifying problems to knowing what to fix first. We are also building executive-level reporting and risk quantification capabilities to support board-level conversations, helping leaders translate complex data into business and financial impact. Tenable protects firmware, BIOS, and embedded systems through deep visibility. Tenable OT Security passively inventories devices, identifies firmware versions, monitors configurations for unauthorised changes, and detects threats via network anomalies—helping teams proactively manage and prevent exploitation.
-----------------------------------------------------------------------------------------------------------------------------------------
Veeam champions radical resilience for proactive cyber threat defense
 SANDEEP BHAMBURE
SANDEEP BHAMBURE
VP & MD - INDIA & SAARC, VEEAM SOFTWARE
At Veeam, our mission is to help organizations achieve data resilience—not just recover from cyber-attacks, data loss, or outages, but emerge stronger and stay ahead of future threats. Recon Scanner, now integrated into the Veeam Data Platform, leverages intelligence from Coveware by Veeam, which maintains one of the world’s largest ransomware incident databases. It proactively scans backup environments for malicious activity, such as unusual file changes or suspicious user behaviour, helping detect threats early. We follow Zero Trust principles—no action is trusted by default, access is restricted, backups are immutable, and all operations are verified. Our Threat Center in Veeam ONE consolidates critical insights across the platform, giving customers a unified view of their environment’s security posture. We also partner with companies like CrowdStrike to combine endpoint protection with data resilience, offering visibility and actionable intelligence across infrastructures.
With cybercriminals growing more sophisticated and the attack surface expanding, we embrace Radical Resilience—helping organizations recover quickly with minimal disruption. Our expanded Cyber Secure Program includes quarterly security assessments, guaranteed incident response within 15 minutes, and ransomware recovery warranties, especially valuable in India and the SAARC region. Secure by Design principles guide our development process, with malware detection embedded before, during, and after backups. While Veeam doesn’t manufacture hardware, we advocate best practices for firmware and BIOS security. We recommend enabling UEFI native mode, Secure Boot, TPM 2.0, and using immutable, hardened repositories. Post BIOS updates, rescanning and validation ensure systems remain fully operational, securing data protection from the hardware up.
-------------------------------------------------------------------------------------------------------------------------------------
Zscaler powers secure innovation with AI- driven Zero Trust approach
 SUVABRATA SINHA
SUVABRATA SINHA
CISO-IN-RESIDENCE - INDIA, ZSCALER
With the rise of cyberattacks becoming more frequent and complex, protecting our digital world requires complete visibility and control. Zscaler’s AI-driven Zero Trust Exchange examines over 500 trillion signals every day, utilizing advanced analytics to detect and mitigate threats before they can impact users, applications, or devices. We analyze all traffic, including encrypted data, to block ransomware, zero-day attacks, and phishing schemes instantly. By leveraging our industry-leading Security Graph and the power of AI, we transform raw data into actionable intelligence—often identifying threats before they are publicly known—and secure our global customer base at scale with unmatched agility.
As organizations increasingly adopt cloud services, IoT, and edge computing, Zscaler helps reduce risks by embedding Zero Trust principles into the architecture from the outset. This approach benefits not only enterprises but also OEM partners aiming to build secure-by-design products that operate safely across complex and distributed environments.
We are committed to integrating every available and emerging technology into our Zero Trust architecture. Like AI, quantum computing brings both significant opportunities and new security challenges. We are actively preparing for the post-quantum era and will be well-positioned to help customers securely embrace that future.
Security should not slow down transformation—it should accelerate it. That is precisely what Zscaler’s approach is designed to do: enable innovation securely, intelligently, and confidently across the evolving digital landscape.
------------------------------------------------------------------------------------------------------------------------------------------
See What’s Next in Tech With the Fast Forward Newsletter
Tweets From @varindiamag
Nothing to see here - yet
When they Tweet, their Tweets will show up here.