A series of data breaches targeting global companies such as Qantas, Allianz Life, LVMH, Tiffany & Co., Dior, Louis Vuitton, and Adidas have been linked to the cyber extortion group ShinyHunters, who exploited Salesforce environments via sophisticated voice phishing (vishing) campaigns.
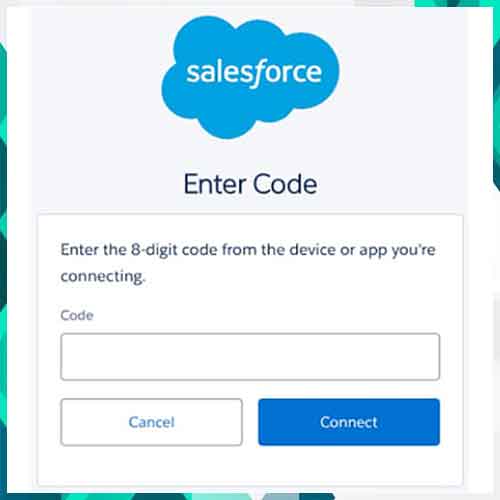
The attacks, tracked by Google’s Threat Intelligence Group (GTIG) as UNC6040, involve social engineering tactics where threat actors impersonate IT support over the phone to trick employees into visiting Salesforce’s connected app setup page. Victims are then asked to enter a “connection code” that links a malicious version of Salesforce’s Data Loader OAuth app—often renamed “My Ticket Portal”—to the company’s Salesforce instance.
In some cases, phishing pages mimicking Okta login portals were also used to steal credentials and MFA tokens. Once inside, the attackers accessed Salesforce database tables like "Accounts" and "Contacts" to steal customer data.
Companies Affected
· LVMH brands including Louis Vuitton, Dior, and Tiffany & Co. confirmed breaches via third-party customer data platforms.
· Adidas, Qantas, and Allianz Life also acknowledged incidents involving unauthorized access to CRM systems, though none have officially named Salesforce.
· Allianz Life confirmed that its U.S. entity’s cloud-based CRM system was compromised on July 16, 2025.
· Qantas has not confirmed Salesforce involvement, but court documents reference Salesforce-specific data tables.
Sources said that, the same campaign impacted all these organizations, with no public data leaks yet. However, extortion emails are being sent under the ShinyHunters name, suggesting that the group may leak or sell the stolen data if ransoms go unpaid—mirroring its tactics in the Snowflake attacks.
GTIG attributes the initial compromise to UNC6040 and follow-up extortion to a related cluster named UNC6240. Both are believed to be part of a broader network that overlaps with Scattered Spider (UNC3944) and possibly the now-defunct Lapsus$ group.
Security analysts believe ShinyHunters may operate under an extortion-as-a-service mode
Salesforce reiterated that its platform remains secure and has not been compromised. Instead, attackers exploit social engineering to gain unauthorized access.
"The issues described are not due to any known vulnerability in our platform. We urge customers to implement strict security measures," said Salesforce.
Salesforce recommends:
· Enforcing trusted IP ranges for logins
· Enabling multi-factor authentication (MFA)
· Limiting connected app access
· Using Salesforce Shield for threat detection and monitoring
· Assigning a dedicated Security Contact for faster incident response
For full security guidance, Salesforce directs users to: Salesforce Social Engineering Protection Blog.
The investigation is ongoing, and more companies are expected to come forward as victims of this large-scale, cloud-focused data extortion campaign.
See What’s Next in Tech With the Fast Forward Newsletter
Tweets From @varindiamag
Nothing to see here - yet
When they Tweet, their Tweets will show up here.